What feel when you here Phishing ?
"You can fool some of the people all of the time, and all of the people some of the time, but you cannot fool all of the people all of the time."
–Abraham Lincoln-The term “Phishing” basically referred to "account theft using instant messaging." Nowadays, phishing occurs through email. Phishing can be defined as an act of sending an email to the user in order to steal his personal information such as bank account details, credit card information etc.Such emails may direct the user to click on a link which is a website where they are said to update their personal information like passwords, credit card details, social security number or bank account number. This type of bogus website is specifically designed for information theft.

Types of Pishing
Deceptive Phishing
A phisher sends bulk email with a message. Users are influenced to click on a link.
Examples: An email stating that there is a problem with recipient’s account at financial institutions and requests the recipient to click on a website link to update his details. A statement may be sent to the recipient stating that his account is at risk and offering to enroll him to an anti-fraud program. In any of the case, the website collects the user’s confidential information. In most of these cases, the phisher does not directly cause any economic damage, but sells the illegally obtained information on a secondary market.
Malware-based Phishing
Malware-based phishing involves running malicious software on the user’s machine. The malware can be introduced as an email attachment or as a downloadable file exploiting security vulnerabilities. This is a particular threat for small and medium businesses (SMBs) who fails to update their their software applications.
Keyloggers and Screenloggers
Keyloggers and screenloggers are varieties of malware that track input from the keyboard and send relevant information to the hacker via the Internet. They can embed themselves into the user’s browsers as small utility programs.
Session Hijacking
Session Hijacking is a kind of phishing attack where user’s activities are monitored clearly until they log into a target account like the bank account and establish their credentials. At that point, the malicious software takes control and can undertake unauthorized actions, such as transferring funds, without the knowledge of the user.
Web Trojans
Web Trojans pop up when the users attempt to log in to an important website or performing any transaction. These web trojans are invisible to the users. They collect user's credentials locally and transmit them to the phisher.
Hosts File Poisoning
When a user types a URL of a website it is first translated into an IP address before it's transmitted over the Internet. The majority of user’s PCs running a Microsoft Windows operating system first look up these "host names" in their "hosts" file before undertaking a Domain Name System (DNS) lookup. Phishers steal information by "poisoning" the hosts file. They transmit a bogus address, taking the user unwittingly to a fake "look alike" website.
System Reconfiguration Attacks
This is a kind of phishing attack where the settings on a user's PC are modified with bad intentions. For example: URLs in a favorites file might be modified to direct users to bogus websites that look alike. For example: a financial institution's website URL may be changed from "bankofxyz.com" to "bancofxyz.com".
What is Data Theft
Malicious code running on a user’s computer, can directly steal confidential information stored on the computer. This information can include activation keys to software, passwords, sensitive and personal email and any other data that is stored on the victim's computer.In addition, confidential memos, design documents or billing info can be publicly leaked, causing embarrassment or financial damage to the organization. This data can also be leaked to competitors.
DNS-Based Phishing
Domain Name System (DNS)-based phishing or hosts file modification is called Pharming. The requests for URLs or name service return a bogus address and subsequent communications are directed to a fake site when the hackers tamper a company’s host files or domain name. As a result, users remain unaware about the fraud website controlled by hackers.
Content-Injection Phishing
Content-injection phishing means inserting malicious content into a legitimate website. The malicious content can redirect to other websites or may install malware on a user’s computer and also insert a frame of content that will redirect data to the phishing server.
Man-in-the-Middle Phishing
Man-in-the-Middle Phishing is hard to detect than many other forms of phishing. In these attacks hackers sit between the user and the website or the system. They record the information being entered by the user but continue to pass the user on to the next steps so that user transactions are not affected and the user remains unaware. Later, they sell or use the information which may be credentials, credit card details, and bank account details.
Search Engine Phishing
Phishers develop e-commerce websites with attractive offers. Later these sites are indexed legitimately with different search engines. When users search for products or services, these sites are shown by the search engine and are fooled into giving up their information. For example, scammers have set up false banking sites that offer lower credit costs or better interest rates than other banks. Victims are often encouraged to transfer account details. In this way, they are deceived into giving up their details.
1. Legit companies don’t request your sensitive information via email
Chances are if you receive an unsolicited email from an institution that provides a link or attachment and asks you to provide sensitive information, it’s a scam. Most companies will not send you an email asking for passwords, credit card information, credit scores, or tax numbers, nor will they send you a link from which you need to login.
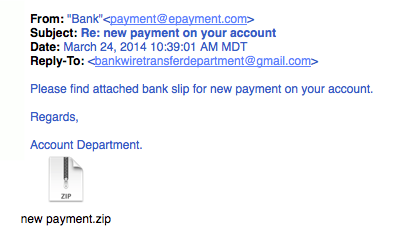
2. Legit companies call you by your name
Phishing emails typically use generic salutations such as “Dear valued member,” “Dear account holder,” or “Dear customer.” If a company you deal with required information about your account, the email would call you by name and probably direct you to contact them via phone.

3. Legit companies have domain emails
Don’t just check the name of the person sending you the email. Check their email address by hovering your mouse over the ‘from’ address. Make sure no alterations (like additional numbers or letters) have been made. Check out the difference between these two email addresses as an example of altered emails: michelle@paypal.com michelle@paypal23.com Just remember, this isn’t a foolproof method. Sometimes companies make use of unique or varied domains to send emails, and some smaller companies use third party email providers.
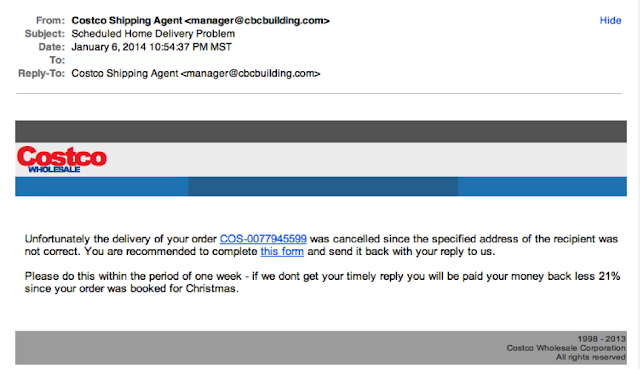
4. Legit companies know how to spell
An email from a legitimate organization should be well written. Little known fact – there’s actually a purpose behind bad syntax. Hackers generally aren’t stupid. They prey on the uneducated because they are easier targets.
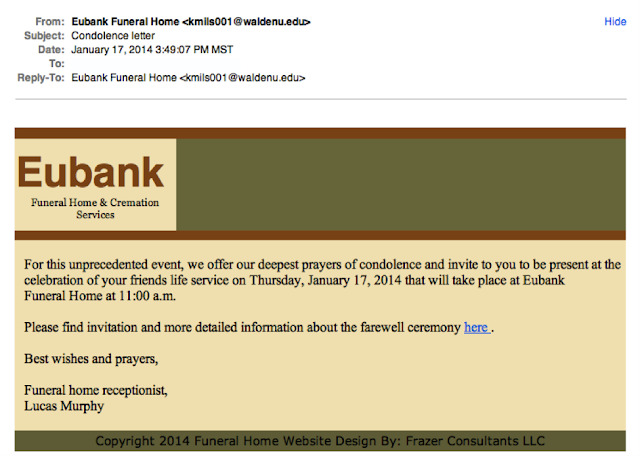
5. Legit companies don’t force you to their website
Sometimes phishing emails are coded entirely as a hyperlink. Therefore, clicking accidentally or deliberately anywhere in the email will open a fake web page, or download spam onto your computer.

6. Legit companies don’t send unsolicited attachments
Unsolicited emails that contain attachments of hackers. Typically, authentic institutions don’t randomly send you emails with attachments, but instead direct you to download documents or files on their own website.
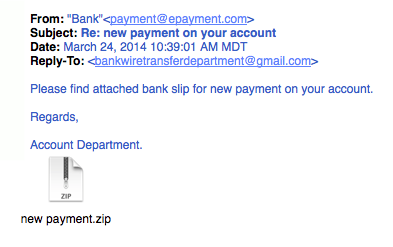
7. Legit company links match legitimate URLs
Just because a link says it’s going to send you to one place, doesn’t mean it’s going to. Double check URLs. If the link in the text isn't identical to the URL displayed as the cursor hovers over the link, that's a sure sign you will be taken to a site you don’t want to visit. If a hyperlink’s URL doesn’t seem correct, or doesn’t match the context of the email, don’t trust it. Ensure additional security by hovering your mouse over embedded links (without clicking!) and ensure the link begins with https://.





as i know these are the things you should have to know,mmmm when some one asked you "do you know how to create phishing site??",he he now on wards you can say yup,because now i am going tooooooooooo ........😉









This is kind of effort to make you aware of how to create a phishing site & how to identify a phishing site.It would be grate full if you would not misuse this information.This blog was done for the support of my assignment & I would like to convey my regards to Mr.Tharindu Edirisinghe who instructed me to make the effort a success.
Much appreciate your feedback as a comment.👩
Thank you!!😊😊
Best Regards,
Pamoda P. Perea
What is Data Theft
Malicious code running on a user’s computer, can directly steal confidential information stored on the computer. This information can include activation keys to software, passwords, sensitive and personal email and any other data that is stored on the victim's computer.In addition, confidential memos, design documents or billing info can be publicly leaked, causing embarrassment or financial damage to the organization. This data can also be leaked to competitors.
DNS-Based Phishing
Domain Name System (DNS)-based phishing or hosts file modification is called Pharming. The requests for URLs or name service return a bogus address and subsequent communications are directed to a fake site when the hackers tamper a company’s host files or domain name. As a result, users remain unaware about the fraud website controlled by hackers.
Content-Injection Phishing
Content-injection phishing means inserting malicious content into a legitimate website. The malicious content can redirect to other websites or may install malware on a user’s computer and also insert a frame of content that will redirect data to the phishing server.
Man-in-the-Middle Phishing
Man-in-the-Middle Phishing is hard to detect than many other forms of phishing. In these attacks hackers sit between the user and the website or the system. They record the information being entered by the user but continue to pass the user on to the next steps so that user transactions are not affected and the user remains unaware. Later, they sell or use the information which may be credentials, credit card details, and bank account details.
Search Engine Phishing
Phishers develop e-commerce websites with attractive offers. Later these sites are indexed legitimately with different search engines. When users search for products or services, these sites are shown by the search engine and are fooled into giving up their information. For example, scammers have set up false banking sites that offer lower credit costs or better interest rates than other banks. Victims are often encouraged to transfer account details. In this way, they are deceived into giving up their details.
several ways to recognize pisihing E-mails
1. Legit companies don’t request your sensitive information via email
Chances are if you receive an unsolicited email from an institution that provides a link or attachment and asks you to provide sensitive information, it’s a scam. Most companies will not send you an email asking for passwords, credit card information, credit scores, or tax numbers, nor will they send you a link from which you need to login.

2. Legit companies call you by your name
Phishing emails typically use generic salutations such as “Dear valued member,” “Dear account holder,” or “Dear customer.” If a company you deal with required information about your account, the email would call you by name and probably direct you to contact them via phone.

3. Legit companies have domain emails
Don’t just check the name of the person sending you the email. Check their email address by hovering your mouse over the ‘from’ address. Make sure no alterations (like additional numbers or letters) have been made. Check out the difference between these two email addresses as an example of altered emails: michelle@paypal.com michelle@paypal23.com Just remember, this isn’t a foolproof method. Sometimes companies make use of unique or varied domains to send emails, and some smaller companies use third party email providers.

4. Legit companies know how to spell
An email from a legitimate organization should be well written. Little known fact – there’s actually a purpose behind bad syntax. Hackers generally aren’t stupid. They prey on the uneducated because they are easier targets.

5. Legit companies don’t force you to their website
Sometimes phishing emails are coded entirely as a hyperlink. Therefore, clicking accidentally or deliberately anywhere in the email will open a fake web page, or download spam onto your computer.

6. Legit companies don’t send unsolicited attachments
Unsolicited emails that contain attachments of hackers. Typically, authentic institutions don’t randomly send you emails with attachments, but instead direct you to download documents or files on their own website.

7. Legit company links match legitimate URLs
Just because a link says it’s going to send you to one place, doesn’t mean it’s going to. Double check URLs. If the link in the text isn't identical to the URL displayed as the cursor hovers over the link, that's a sure sign you will be taken to a site you don’t want to visit. If a hyperlink’s URL doesn’t seem correct, or doesn’t match the context of the email, don’t trust it. Ensure additional security by hovering your mouse over embedded links (without clicking!) and ensure the link begins with https://.

How we prevent ourself??
- Be alert for spam messages.
- Do not reply to emails that request financial information, even if it appears to be from a trusted source.
- Do not reply to emails from unrecognized senders.
- Phishing attempts are not likely to be personalized.
- Do not open any links in suspicious emails, instant messages, or chat-room messages.

- Only communicate personal information over the phone or through a secure website.
- Secure websites are indicated by a lock on the browser's status bar or the prefix "Https://" instead of Http://.
- It is safe to give personal information on the phone only if you initiate the call to a secure phone number. For example, it is best to call a number located on your bank statement rather than a number that you were asked to call in an email.

- Never use email to share personal information.
- Even if you know the recipient of an email, unauthorized individuals may be able to gain access to your or the recipient's email account.
- Individuals with advanced technical skills can intercept your email.

- Avoid using email on public computers.
- Information from an email is temporarily stored on a computer's local disk and can be retrieved by another user if it is not properly deleted.

- Do not click anything in pop-up windows.
- If your browser has a pop-up blocker, enable it.
- Do not copy any website addresses from a pop-up window into your browser.
- A legitimate enterprise will never ask you for your information in a pop-up window.
- Use security programs to protect your computer.
- Use a spam filter, anti-spyware program, anti-virus program, and a firewall. These can be obtained from a software retailer or on the Internet.
- Check your credit report and financial statements regularly.
- Make sure that no unauthorized transactions have been made and that all items on your credit report are correct.

as i know these are the things you should have to know,mmmm when some one asked you "do you know how to create phishing site??",he he now on wards you can say yup,because now i am going tooooooooooo ........😉
Creating Pishing site
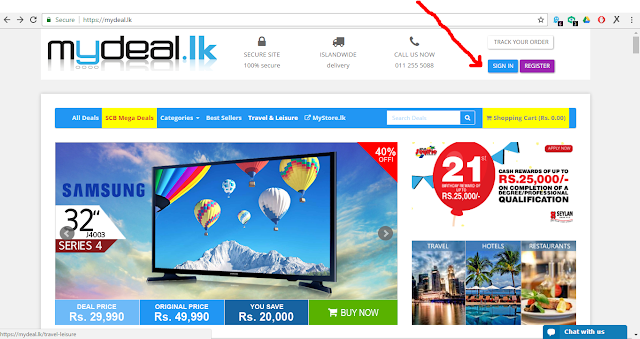
- First of all you have to select web site which have login page(sign in).

- Then click sign in button and go to sign in page,in there you can see login form😊,right click the page and hit save as.
- When saving, select the type as ‘Web Page, complete’, so that the web content referred in the web page (like images, CSS, javascript files) also will be downloaded.

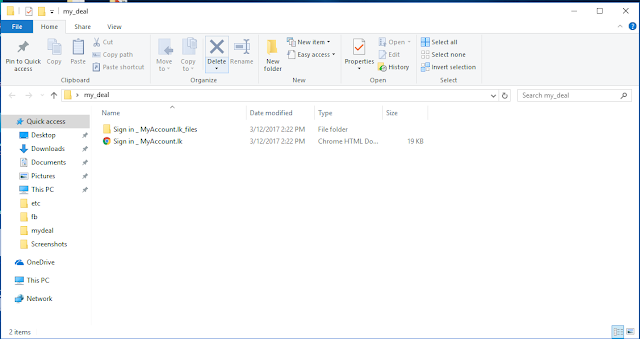
- Once you save the login page, you will see the html file which contains the login page and the web resources are stored in a folder in the same location.
- now you can create a folder and put those two files to it.

- If you open the downloaded HTML file in the browser, you will see the same login page of mydeal.lk website where you will not notice any difference unless you check the web URL.

- Now open the login page (html file) and locate where the HTML form is that contains the username and password text boxes. (If the source code is not formatted, you can use an IDE and format the code).

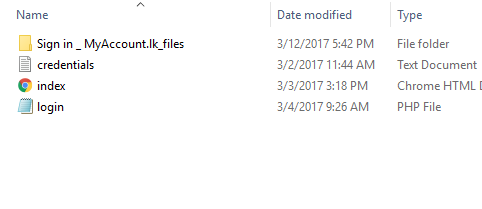
- Here we simply modify the action of the HTML form and change to a new PHP file which we create. Here I give the file name as login.php.

- I created the file with name login.php and the following content.write code for storing the credentials in to the credentials.text file.After storing the credentials it redirects the browser to the mydeal voucher page.
- finally you have these files in your folder.

- Now we have to host these files like 000webhosting site.In there we have to create account using your gmail and then create your own site giving any name and add this all files in to public.html folder.After clicking that link you can launch phishing web site.

- This is the link which you can send to the victim.

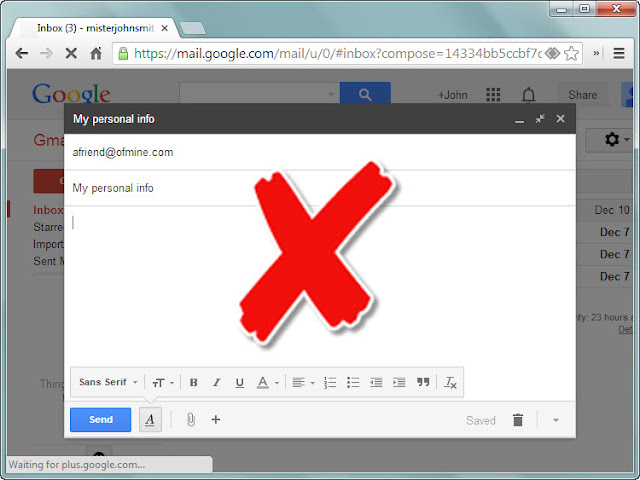
- Now you can send a phishing email using this link. Actually I did this to my some colleges and they entered their emails and password to without any knowledge of phishing emails.
- Here is the email which i sent to the my victim.I got the screen shot from it.😉
- This is the phishing web site which I created and which my victim logged in.

- when you log in to that site you will redirect to the original gift voucher page in mydeal.lk

- when some one login to that site that credential file fill with username and password

This is kind of effort to make you aware of how to create a phishing site & how to identify a phishing site.It would be grate full if you would not misuse this information.This blog was done for the support of my assignment & I would like to convey my regards to Mr.Tharindu Edirisinghe who instructed me to make the effort a success.
Much appreciate your feedback as a comment.👩
Thank you!!😊😊
Best Regards,
Pamoda P. Perea


